Integrate Azure API Management into Internal VNET | Azure API Management Internal Mode

Azure API Management can also manage internal APIs which are not accessible over the Internet. In this blog, we will learn
- What is an internal mode for API Management?
- What are the suitable business cases for API Management internal model
- how to configure it with the step-by-step demo.
If you prefer to watch the video, here it is - A step by step guide on how to configure Azure API Management Internal Mode
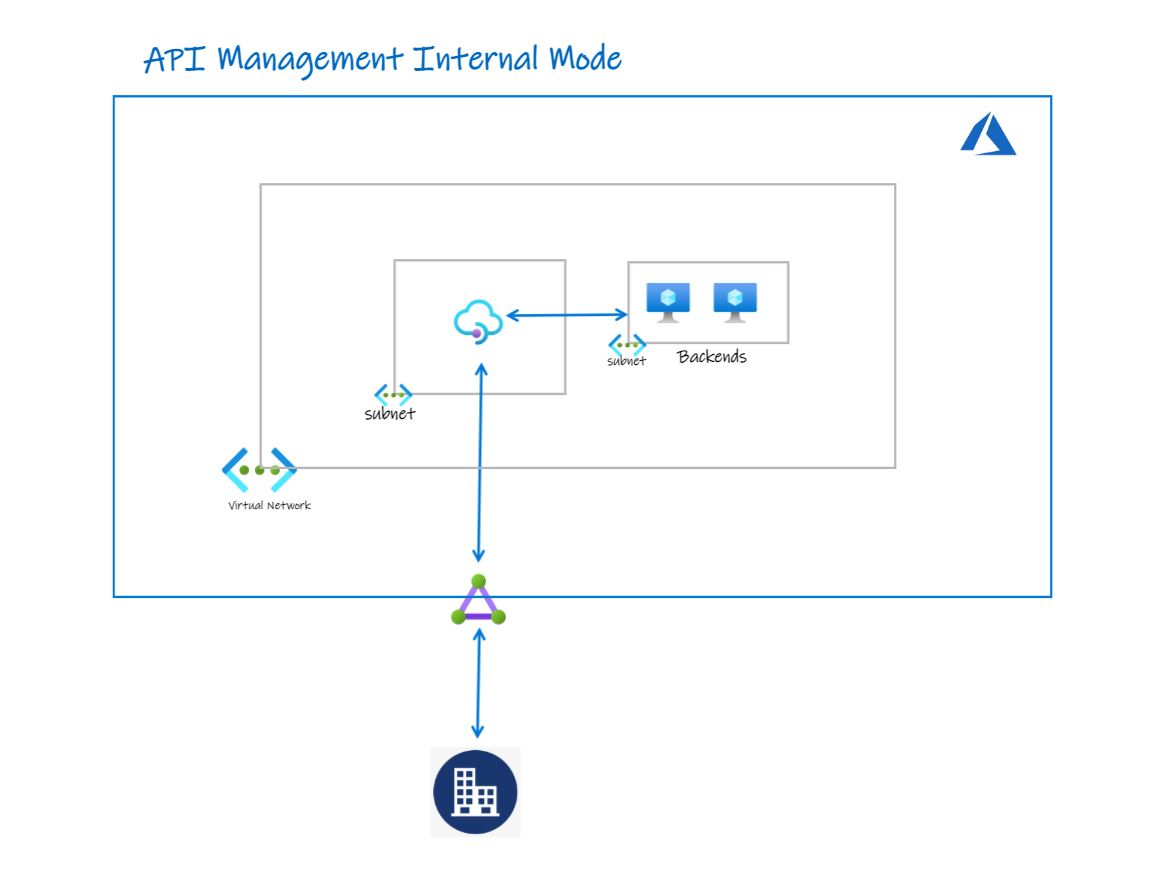
Azure API Management Internal Mode
With internal, we can inject Azure API Management instance into a virtual network and manage the APIs which can be accessed only with-in VNET Connected resources. When the internal mode is enabled in the Azure API Management instance, the access over the internet is completely blocked.
Couple of important points to be noted..
- API Management can be injected into a Virtual Network with Internal Mode turned ON.
- This feature is available in both Premium and Developer tiers of API Management.
- It will have both Public IP Address and a Private IP Address.
- Public IP Address is used to facilitate traffic to the control pane of API Management over port 3443.
- Private IP Address — it is a load-balanced IP Address from the subnet (in which you deploy API Management) to access API Gateway.
- When API Management is deployed in Internal mode, it can be accessed only via a Fully Qualified Domain Name. It can’t be accessed over a Private IP Address. We need to configure this using Azure Private DNS Zone. Just stay with me, you will understand this better during the demo.
- When configured in Internal Mode, the Test console inside API Management will not work as this URL is not registered in Public DNS.
- The developer Portal is accessible only from Virtual Network.
Suitable Business Use Cases
To understand this better, we need to know how the traffic flow in Internal Mode.
Inbound and Outbound traffic can be allowed to peered through virtual networks, Express Route, and VPN S2S Connections.
One of the most common use cases is
Managing On-premises API and providing secure access to the third parties which have connectivity to VNET (peered),
We can also manage both On-premises APIs and cloud-based APIs
Demo
For the purpose of demo, we will create two virtual machines in the same VNET as API Management instance. One VM will act as a web server with a API hosted. We will use this API as backend for our API Gateway and access it using API Gateway url from another virutal machine (client) inside the same VNET.
Part I: Create the Resource Required
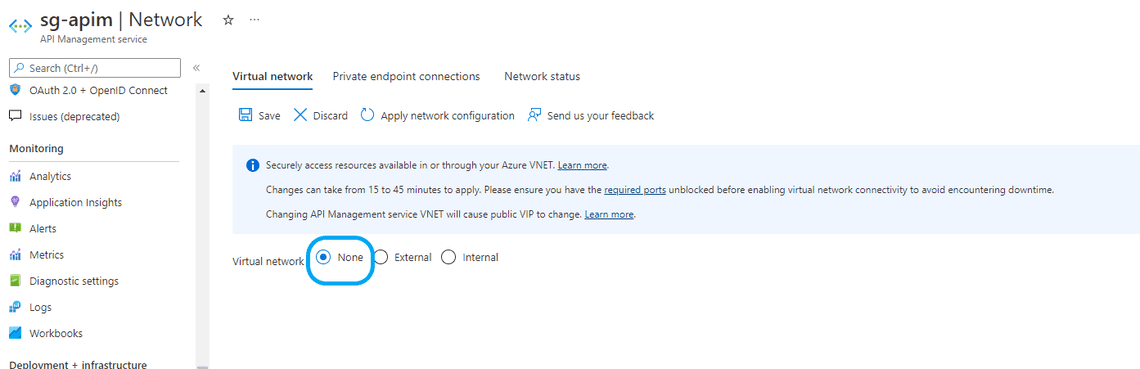
- Create Azure API Management without any Virtual Network Integration. It should be either Premium or Developer to support Internal Mode.
Access one of the APIs over the internet and test it.
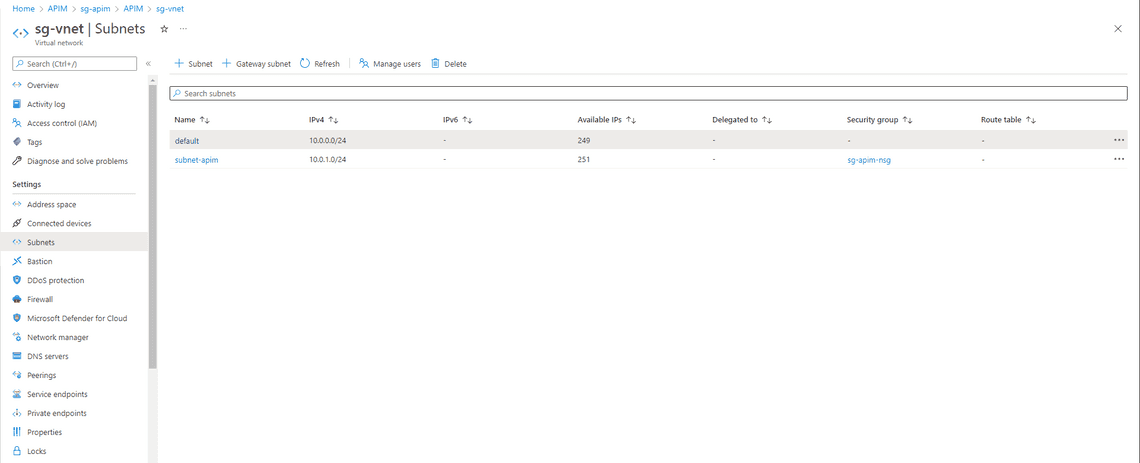
- Create Virtual Network in the same region as API Management and create a Subnet for API Management. I named VNet as sg-vent and subnet as subnet-apim.
- Create two virtual Machines in the default subnet. One VM will act as a Web server and another one will act as an app client.
- Deploy a .NET API into the web server virtual machine.
- Check the connectivity to this API from the app client VM by browsing one of the APIs.
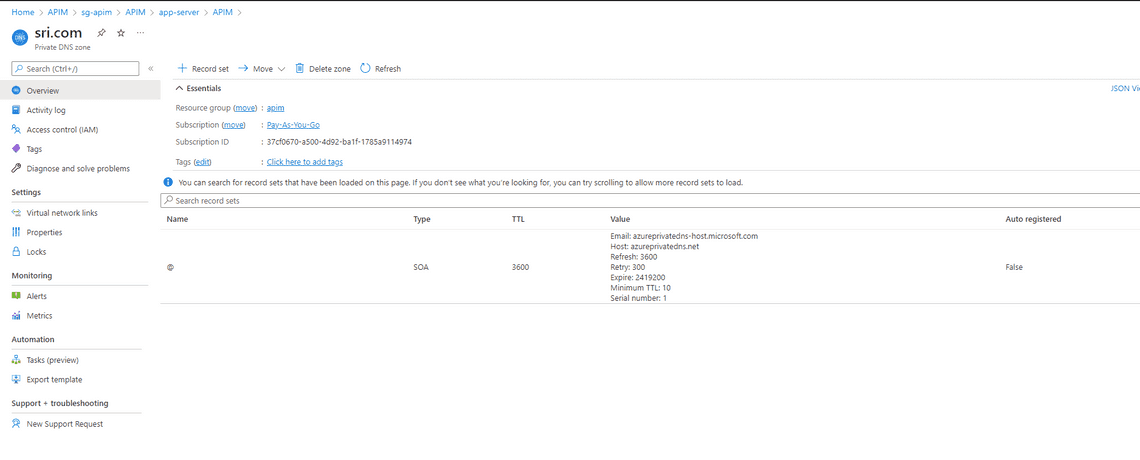
- Create a Private DNS Zone resource with a domain name - In my case, I have created with sri.com name
Part II: Configure Azure API Management Internal Mode
- Go to Azure API Management Instance —> Go to Virtual Network, Select Internal and add it to sg-vnet/subnet-apim
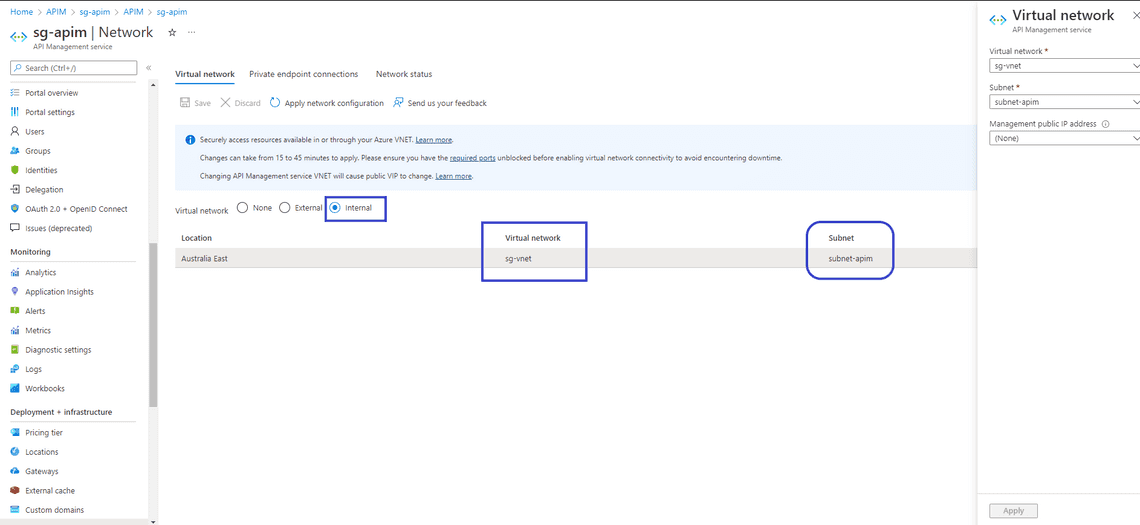
- Create a Network Security group and apply to subnet-apim to restrict inbound and outbound traffic from/to API Management. I have named NSG as sg-apim-nsg
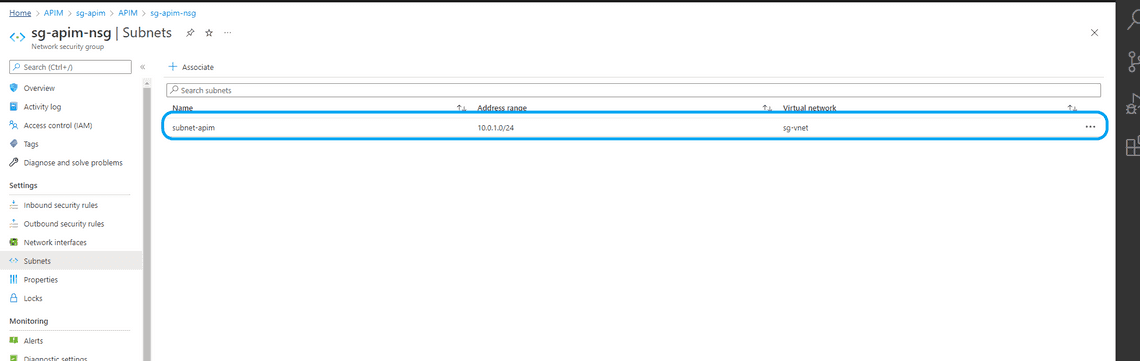
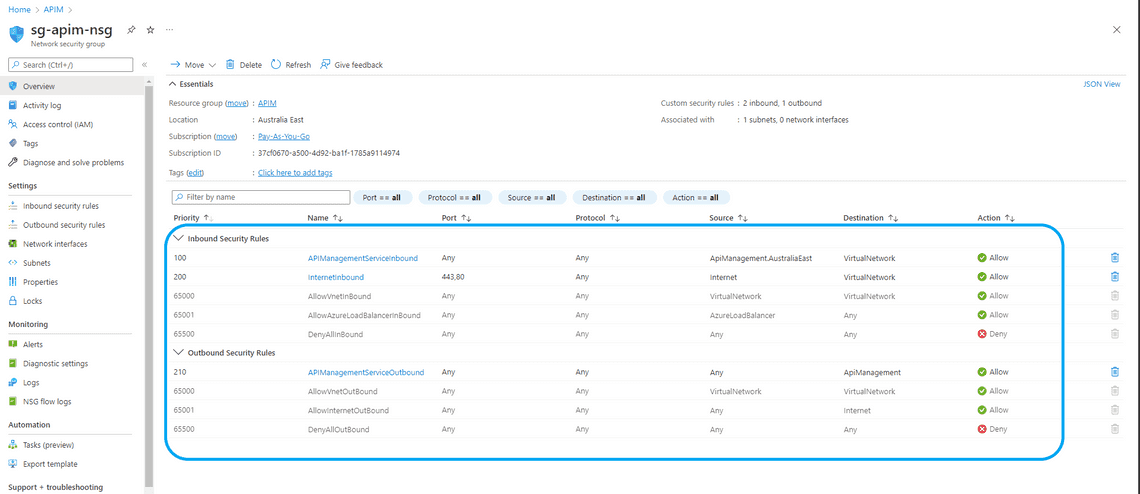
Apply Inbound and Outbound traffic rules as shown below.
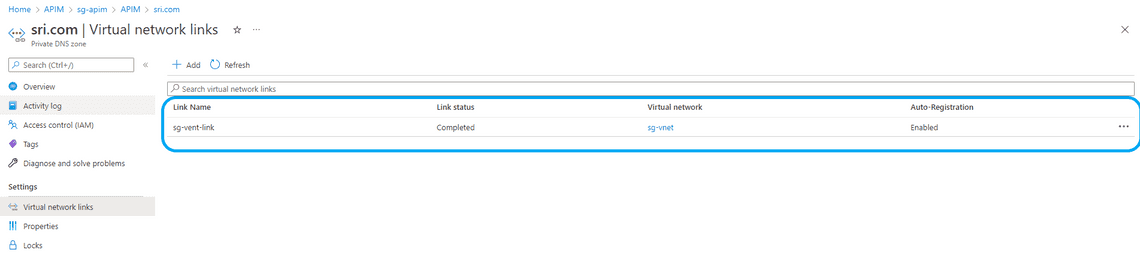
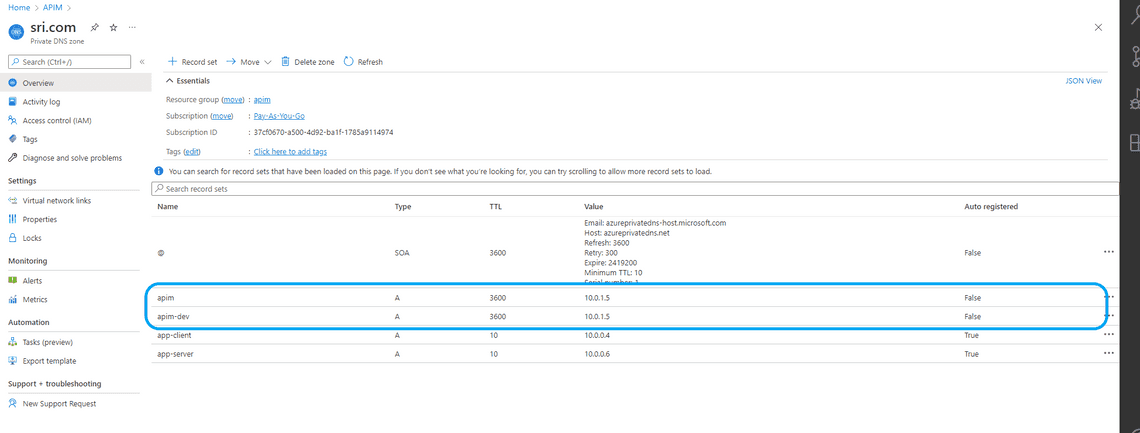
- Go to sri.com Private DNS Zone resource and connect the sg-vnet to the private DNS zone
- Locate the private IP address of Azure API Management and create two private DNS records. One for API Gateway and another one for the developer portal. 10.0.1.5 is the Private IP Address of Azure API Management.
- Now create a self-signed certificate for sri.com domain.
To make things easier, we create 2 certificates with the following PowerShell script. One of the certificates is a root certificate for signing, and the other is a wildcard certificate (CN=*.sri.com) for SSL bindings of the custom domain names.
# Create the root signing cert
$root = New-SelfSignedCertificate -Type Custom -KeySpec Signature `
-Subject "CN=contoso-net-signing-root" -KeyExportPolicy Exportable `
-HashAlgorithm sha256 -KeyLength 4096 `
-CertStoreLocation "Cert:\CurrentUser\My" -KeyUsageProperty Sign `
-KeyUsage CertSign -NotAfter (get-date).AddYears(5)
# Create the wildcard SSL cert.
$ssl = New-SelfSignedCertificate -Type Custom -DnsName "*.sri.com","sri.com" `
-KeySpec Signature `
-Subject "CN=*.contoso.net" -KeyExportPolicy Exportable `
-HashAlgorithm sha256 -KeyLength 2048 `
-CertStoreLocation "Cert:\CurrentUser\My" `
-Signer $root
# Export CER of the root and SSL certs
Export-Certificate -Type CERT -Cert $root -FilePath .\sri-signing-root.cer
Export-Certificate -Type CERT -Cert $ssl -FilePath .\sri-ssl.cer
# Export PFX of the root and SSL certs
Export-PfxCertificate -Cert $root -FilePath .\sri-signing-root.pfx `
-Password (read-host -AsSecureString -Prompt "password")
Export-PfxCertificate -Cert $ssl -FilePath .\sri-ssl.pfx `
-ChainOption BuildChain -Password (read-host -AsSecureString -Prompt "password")
- Set up custom domains for both App gateway and developer portal of Azure API Management instance.
The certificate type is custom and select sri-ssl.pfx file created above and click save
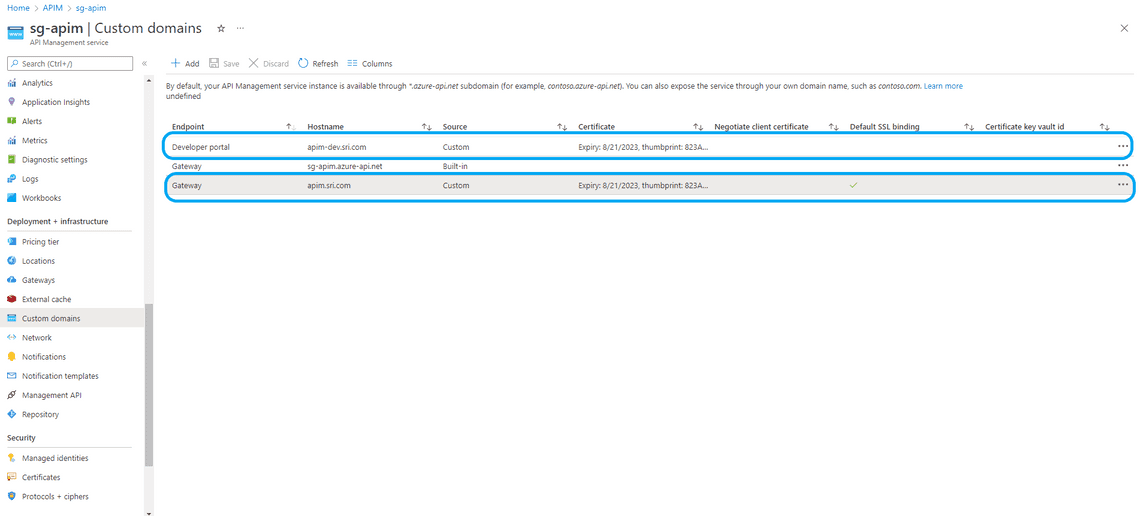
Now in the API Management overview section, your can see configured custom domains.
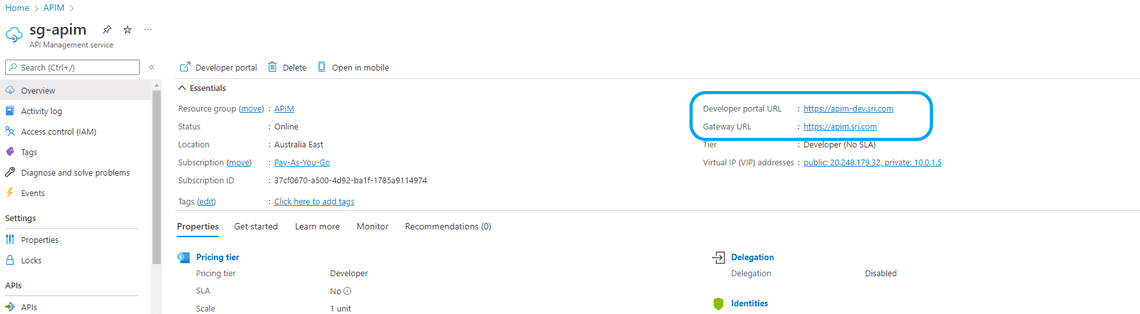
With the above, the set-up is complete. let’s verify this.
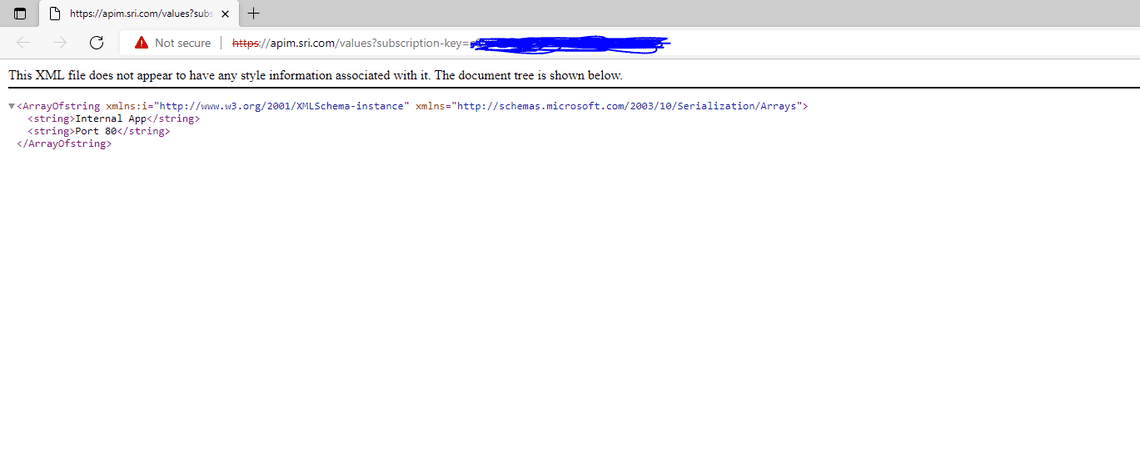
- RDP into app-client and Connect to the API with a private DNS name.
Newsletter
Related Posts
Legal Stuff

