Azure Functions Virtual Network integration | Private Endpoints for Azure Functions

We can host the function app mainly in two ways.
- In Multitenant infrastructure
- Consumption Plan — scales dynamically in response to load and offers minimal network isolation options.
- Premium Plan — scales dynamically and offers more comprehensive network isolation.
- App Service Plan — operates at a fixed scale and offers network isolation similar to the Premium plan
- In App Service Environment — This method deploys your function into your virtual network and offers full network control and isolation.
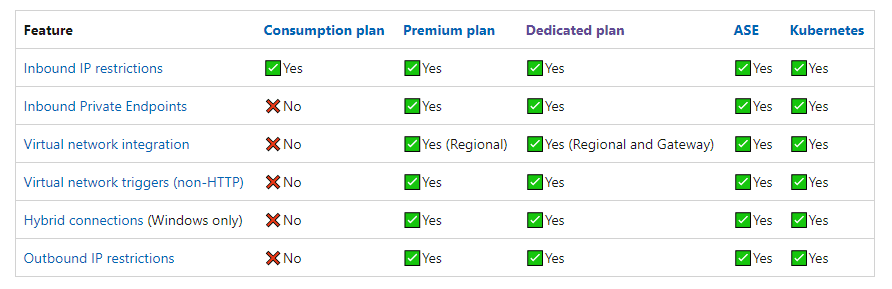
VNET Integration options
Azure Function VNET integration is supported by Premium Azure functions, App Service Plan minimum Basic tier and of course App Service Environment. When we create an azure function without any VNET integration, it will have a public IP address and it will be exposed to the internet.
This Blog will explain
- How we can secure the Azure function with VNET integration?
- How we can create a private endpoint to secure incoming traffic?
- How can we restrict outbound traffic from the Azure function to VNET?
Why do we need Azure function VNET Integration?
- Access to VNET-based resources
- Lock down your function app behind a VNET (no public IP Address at the source or destination)
- Access to Azure PaaS services(for example, Azure Storage and SQL Database) over a private endpoint.
- Access services running on-premises over ExpressRoute private peering, VPN tunnels and peered virtual networks.
Inbound Traffic
Inbound traffic is controlled using Accessing Restrictions and Private Link.
Access Restrictions: You can use access restrictions to define a priority-ordered list of IP addresses that are allowed or denied access to your app. When there are one or more entries, an implicit “deny all” exists at the end of the list. IP restrictions work with all function-hosting options.
What is a Private Link? Azure PaaS services are shared services and they are available over public IP addresses. Private Link enables us to connect to Azure PaaS services(storage, SQL, logic apps, service bus, event grids etc..) without opening to the Internet. A private link will give a private IP address to the Azure PaaS service and traffic will go through the Microsoft backbone network. So, No internet exposure.
Outbound Traffic
Outbound IP restrictions are available in a Premium plan, App Service Plan, or App Service Environment. You can configure outbound restrictions for the virtual network where your App Service Environment is deployed.
When you integrate a function app in a Premium plan or an App Service plan with a virtual network, the app can still make outbound calls to the internet by default. By integrating your function app with a virtual network with Route All enabled, you force all outbound traffic to be sent into your virtual network, where network security group rules can be used to restrict traffic.
Steps for Azure Functions Virtual Network integration
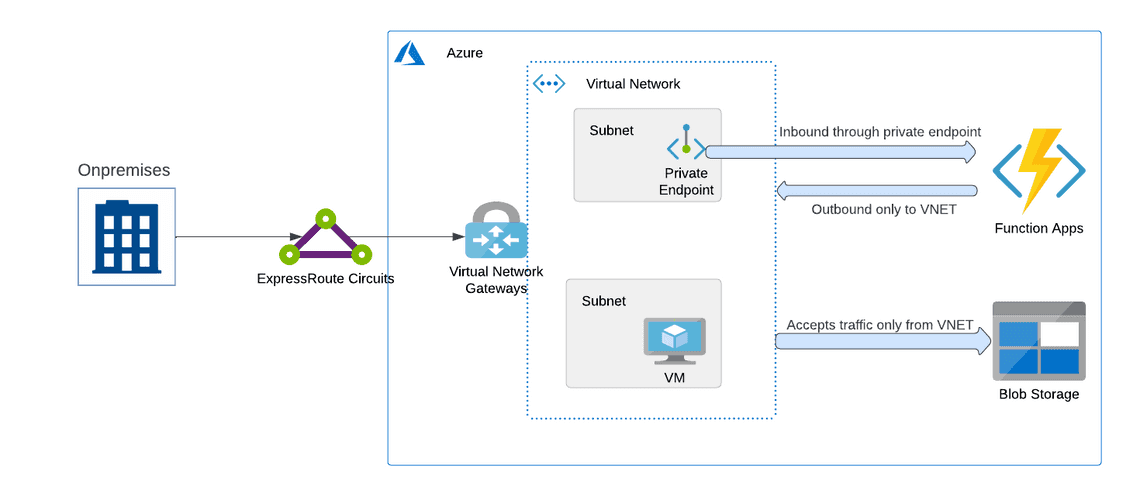
The above architecture demonstrates the steps involved at a high level.
Create a simple azure function that retrieves the data from the Azure storage table.
Inbound Traffic
- The azure function is with App Service Plan Free tier. It is accessible over the internet.
- Create a private endpoint for the Azure function and place this in a virtual network.
- As soon as we create a private endpoint, the Azure function is access is blocked over the internet. The azure function is accessible only from the vent where the private endpoint is placed.
- To demonstrate Azure function access from a virtual network, create a virtual machine without a public IP address inside the same virtual network
- As the virtual machine is a private one, create a Bastion resource to access the VM.
- Now access the azure function from VM.
Outbound Traffic
- Integrate the function app into the virtual network, so traffic from the function app is restricted only to the virtual network
- restrict the azure storage account access to virtual
- Now we can access the azure function from VM.
The video above will give you a step by step walk though of these steps - watch it here
Newsletter
Related Posts
Legal Stuff

